Frequently Asked Questions
What are Organisational Measures?
These measures are an organisation’s approach to evaluating, developing, and implementing controls to protect personal data for the purpose of prevention or prohibition.
Therefore, raising awareness and training employees will be the key organisational measure that should be implemented on a regular basis with respect to other measures.
Every company must inform all employees who have access to personal data that they have obligations and responsibilities for the processing of such data.
Some of the organisational measures are classified as follows:
- Security policies and regulations for employees and users of information systems: (safe password policy, data destruction policy, policies for the good use of email and internet, clean desktop policy, etc..)
- Rights of data holders: Employees must be aware of the procedure for dealing with the rights of the data subjects. For example, in cases of right of access request, rectification or suspension or deletion of data, by the subject.
- Involvement of senior management: This is a key aspect for the success of the company, as they must be involved in the development of these measures and demonstrate good practice.
What are the Technical Measures?
Generally, it is defined as the measures and controls provided to the systems and technological aspects of a company, such as devices, networks and hardware. These measures include both physical and IT security
From the perspective of “physical” security, the following factors must be taken into account:
- The quality of the locks and doors, the protection of the office with alarms and CCTV
- How to control access to the office and how guests are supervised
- How to dispose of electronic and paper waste
- How to keep computer equipment, such as cell phones, safe.
In the IT context they can sometimes be categorized as “cyber security” measures. So we have to take into account factors such as:
- Security systems: for example the security of our network and information systems, not to mention those that process personal data.
- Data security: the security with which you store the data in your systems. For this you have to: Have secure passwords and keep them confidential, separate personal and professional uses by managing users, roles and privileges, protect your email with anti-spam and anti-phishing systems
- Online security of your website: Filtered access to malicious sites, downloads with code, alerts to detect malicious traffic, security for Wi-Fi networks to prevent unauthorized access or uncontrolled devices and possible attacks.
- Device security: Updating devices and computers, have an anti-virus system and update it regularly, have a firewall for computers where automated data processing is carried out, encryption of data, files and/or USB devices in case it is necessary to take the data out of the office where it is processed
Whatever the nature of your activity, you must remember that
- Cyber security measures must be appropriate for the size and use of the network and information systems.
- Security must be appropriate to the practice of your company’s activity. For example, if you offer remote work, make sure that the security of the data used in the company is not compromised.
How to determine suitable technical and organisational measures?
According to Article 32 of the GDPR, technical and organisational measures should be determined taking into account the following criteria:
- Application costs
- Type, scope, context and purpose of processing
- Probability and severity of the risk to the rights and freedoms of natural persons
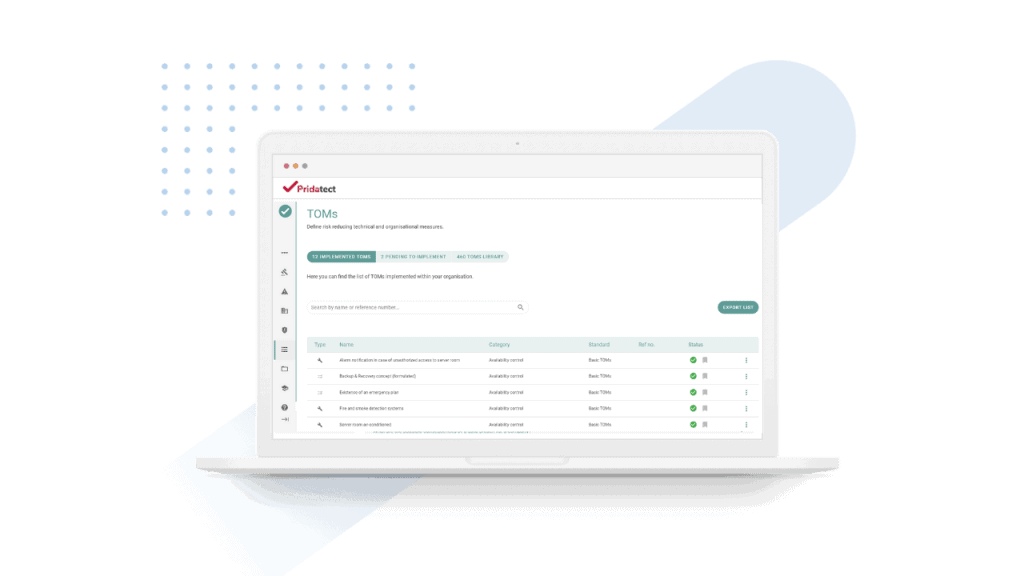
GDPR does not contain a precise list of TOMs that have to be implemented in companies, since all measures are variable and have to be applied according to the judgement of the controller.
Examples of technical and organisational measures
These are some examples of technical and organisational security measures under GDPR:
TM – alarm systems
TM – biometric access control
TM- video surveillance of access to facilities
TM – access with personalised username and password.
TM – software antivirus for mobile devices
OM – “Secure Password” policy
OM – “data deletion” policy
OM – access control by reception / porter
OM – visitor registration / visitor log
OM – worker and visitor badges